This blog post contains a list of basic but practical questions & answers in the field of Networking.
Compare LAN and WAN
LAN (Local Area Network) is a network of computers in a small area like a house, a building, or a campus. WAN (Wide Area Network) is a network of much bigger regions like a country or continent. The internet is the largest WAN (also called GAN – Global Area Network).
Describe VPN
VPN (Virtual Private Network) securely extends the use of a private network over the public internet. Suppose our organization is based in Munich as has a private network over there. Today, as you are working from home in Paris, in theory, you cannot access the private network in Munich. However, this is possible through the use of a VPN.
What are the use cases of VPNs?
Below are the most common use cases for VPNs:
- To securely connect between different offices located at different geographical locations.
- It is safer to transmit confidential information through VPNs in public (Wifi) networks.
- It keeps your identity anonymous on the internet.
What are the types of VPN?
There are 2 big types of VPN: Access VPN and site-to-site VPN.
The Access VPN allows individual users to access a private network (e.g. employees can access the organization’s private network from home).
The site-to-site VPN is for connecting different offices from different geographical locations to a unified private network. This type can be further subdivided into Intranet VPN (these offices are of the same company) and Extranet VPN (customers, partners connect to the intranet of a company).
Describe Proxy servers. How are they different from VPN?
Using a Proxy server is very similar to using VPN. They both stand between end-users and the wild internet. Since every action of the end-users is done by the proxy server (or VPN), the outside internet is completely blind about what the users do, except that they know the users are using a proxy server (or VPN).
The differences between them are:
| Proxy servers | VPNs |
|---|---|
| Only the browser or the app that turns on the proxy will be protected. | Cover all internet traffic from the computer that uses VPN. |
| Can be set up to blacklist or whitelist some websites. | |
| VPN encrypts your data, so it is more secure. |
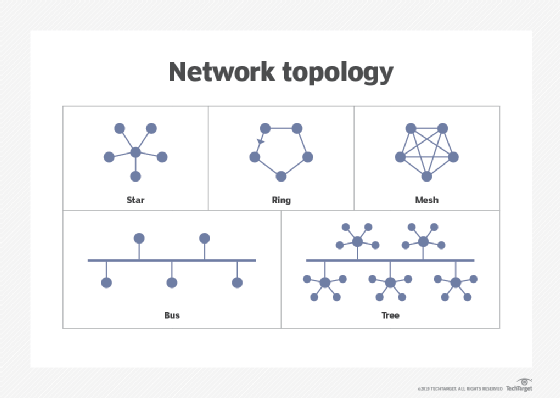
Describe network topology and its types
A network topology is a physical layout of a network that describes how the nodes (or endpoints, or devices) are linked to each other.
Popular types of network topology are bus, star, ring, mesh, and tree (or bus-star).
What are Private and Special IP addresses?
Private addresses are not usable on the internet, they are for private use only. Private address ranges are:
10.*.*.*172.16.0.0->172.31.255.255192.168.*.*
where * can be exchanged for any integer from 0 to 255.
Special IP addresses (127.0.0.1 -> 127.255.255.255) are loopback addresses (i.e. any message sent to these addresses is returned back to this computer). 127.0.0.1 is usually known as the local host.
Briefly describe HTTP and HTTPS
HTTP (HyperText Transfer Protocol) is a set of rules to transfer information over the internet. It is an application protocol built upon the TCP (Transmission Control Protocol).
HTTPS is an improved version of HTTP with SSL/TLS on top for security.
What is the DNS?
The Domain Name System (DNS) is a hierarchical and decentralized naming system that translates a domain name to its IP address. Thanks to the DNS, we only need to remember the human-friendly names of the websites rather than their IP addresses in order to access them.
Distinguish distributed and decentralized systems
Both types allow components of the system to locate in multiple machines. However, while in a decentralized system a single machine has the ability to make decisions on its own, in a distributed system the decisions are made by the central node using knowledge from some or all the machines.
Compare routers and gateways
Both routers and gateways are used to direct network traffic among devices or networks. The main difference between these two is that while a router can only transmit data between networks with the same protocol, a gateway can work for dissimilar networks.
What is a Modem?
The Modem is the device that encodes, sends, receives, and decodes data to and from the outside internet. We need a modem to access the internet. Quite often, a router is connected to the modem to distribute the internet connection to more devices.
Nowadays, many modem models can also do the work of a router and vice versa.
What is the three-way handshake, TCP, and UDP
TCP (Transmission Control Protocol) is a set of rules to reliably transmit data over the internet. To ensure the data sent over is not corrupted (i.e. the transmission is reliable), it uses the three-way handshake process to establish the connection.
Let’s assume A has some data to be sent to B. This data is divided into smaller packets before being transmitted over the internet. From its side, A randomly creates an Initial Sequence Number, called X. The three-way handshake process works like below:
- A send X to B. This is called a SYN packet.
- B receives and reads the value of X. B then randomly creates a number Y. B sends X+1 (to acknowledge that B now knows the value of X) and Y over to A. Since both X+1 and Y are transmitted at once, we call this a SYN-ACK packet.
- A receives, reads Y and sends Y+1 to B to let B know that A now knows the value of Y, i.e. A received the SYN-ACK package successfully. This is an ACK package.
After this connection establishment, A can reliably send the data packages to B by prepending X+1 to the first package, X+2 to the second packet, and so on before sending. B can also send packets to A with prepended Y+1, Y+2, etc.
UDP is an unreliable protocol to transmit data. It is mostly similar to TCP, except that there is no handshaking and error checking. One application of UDP is for broadcasting (e.g. movie, live-stream).
Explain DHCP
DHCP (Dynamic Host Configuration Protocol) is used to auto-configure the IP addresses for devices in the network, making them able to communicate over the network.
Differentiate MAC Address and IP Address
MAC addresses are physical addresses, every device has a fixed MAC throughout its lifetime. On the other hand, IP addresses are logical addresses and are assigned to the devices when they connect to a network.
What is unicast, anycast, multicast, and broadcast?
For all casting types, there is a single source that transmits the data. The differences lie in the receiver(s) of the data:
- Unicast: the data is transmitted to a single receiver.
- Anycast: the source is connected to any other device (typically the nearest device), and then usually a unicast connection is established between them to communicate.
- Multicast: there are multiple receivers.
- Broadcast: all devices are receivers.
How do web browsers handle a website request?
When we type any website or URL onto the search bar and hit Enter, a typical browser will do the following:
- Look up the content of that webpage in cache. If it is there, show the content.
- Else, get the IP address of that website either by looking up in cache or perform a DNS lookup.
- Create a TCP connection with that IP address and exchange HTTP requests to get the content to show to the user.
- Cache.
What is a Subnet Mask?
A Subnet Mask is a mask (i.e. 1-bit and 0-bit) on the IP address to separate the IP address into 2 parts: the network part and the host part.
For example, assume a subnet mask of 255.255.0.0, then the first 2 bytes in the IP address define the sub-network address, while the last 2 bytes are to distinguish the devices in the same sub-network. Hence, the IPs 123.321.34.12 and 123.321.178.1 are in the same sub-network, while 123.322.12.34 is not.
What is NAT?
NAT (Network Address Translation) is a protocol to map (one or multiple) private IP address(es) to a single public IP address before sending the data over the internet. The routers in our houses use NAT.
What is the Ethernet?
Ethernet is the technology to connect computers together. To do so, we just plug a wire with the Ethernet ports into the computers. Nowadays, all wired LANs use Ethernet.

What is IPv6?
IPv6 is the Internet Protocol version 6, which is to replace IPv4. The main advantage of IPv6 is that it can represent a lot more IP addresses. IPv6 address size is 16 bytes, while this is only 4 bytes in the case of IPv4.
Briefly describe the RSA algorithm
The RSA algorithm is an asymmetric cryptography algorithm. It makes use of a private key and a public key. The RSA algorithm exploits the fact that it is very difficult to factor large semi-primes (i.e. numbers that are the product of 2 primes).
This algorithm is very common for making digital signatures.
Compare the 2.4 GHz and 5 GHz wireless band
The 2.4 GHz band provides coverage at a longer range but has a slower speed. On the other hand, the 5 GHz works in a smaller area but is faster.
References:
- Networking Interview Questions, interviewbit.
- Top 135 Networking Interview Questions and Answers, guru99.